In the industry, data has always taken up a lot of space. But with limited resources, there wasn’t much done in the security domain. This had positioned many industries at risk of hacking and facing a huge loss. Even storage and security were considered as two different domain. They might have worked together for the benefit of companies but they have their own differences as well. Well, this was until Big Data was introduced. It has bought a change in the networking and implementation of enterprises that depend on data.
The large volume of data is several projects that help the architecture of a network. It requires cloud-based assets and virtual storage to complete the big data projects. In simple words, the big data network is extremely crucial for the monitoring purposes. However, to make sure that the security of the enterprises is not jeopardized due to anything, companies take various measurements. As a matter of factor, with the advancement of Big Data and technologies, security has come out of it as a whole new business. Companies are coming up with several sophisticated data security points that can be extremely helpful for them.
Now the main question that arises is – whether big data is a savior of data security or is it a threat? If not, then what is actually the threat to Big Data?
Consider Big Data as a lake that is filled up with water (data sources). There are so many areas through which amount of water can be accessed, leaked or even stolen. Similarly, Big Data is a problem because in the lake full of data, it is easy to access and utilize it as per our wish and demand. Yes, many people believe that data sources are accessed with the help of cloud or network connections. But as a matter of fact, Big Data can bring our various points that can leave a company or module vulnerable. Even if a contract or a document is under the norms of a breach then Big Data can put up a substantial hold on it.
Apart from this, Big Data is here to help out the business in so many ways that predicted. There is no doubt that for data management, security is the major points that comes above all. This can be easily proved with the main principles of Data security that are followed up through Big Data platform by enterprises.
Authentication
This is all about user verification. When a user signs up for a service or product, identification of that user is required that might take some time which makes the user simply opt for an alternative. However, with the help of Big Data, the verification process is as simple as a cakewalk. There is already a volume of data that can be easily analyzed and verified with a user.
Many companies are also focusing on the sign-on options to ensure that the security of their platform is maintained. They review and evaluate the data from end-to-end to keep security intact. These review option also include analytical tools and dashboards. For a previous user, a cryptography tool is also used to make sure that same person is logging in to the account. They usually have a unique ID and Password or in some case signature key.
Authorization
Another step that companies have taken with the help of Big Data is the authorization of data to only business personnel. The legal information and confidential files are only shared amount high authority personnel or managers. In a few cases, even employees are included but it has its own sets of terms and conditions. In addition to this, they also require the logical structure to accomplish the goals with the help of authorization.
The only drawback is that physical separation can’t be controlled via any sort of authorization. But authorization can handle the tasks that can be performed by a user or even the resources that can be used. For instance, a user can easily handle their own eCommerce account since they have the authorization to do so whereas they can’t operate the account of the person sitting across the globe.
This process can be hacked by in order to understand the algorithm and loopholes of such system definitely takes a lot of time. Now you may feel that a hacker can take their time to find the loopholes. Well, it is not that simple, since they are modified and updated after a span to time to make sure it is highly protected.
Encryption and Data Masking
The main concern of business after such measure is internal theft of data. To secure a large volume of data in a business environment can be a daunting and challenging task for a business personnel. However, to overcome such a situation, companies are now dependent on another of the feature of Big Data – Encryption. In this, two type of techniques are used in rest encryption and in-transit data.
These techniques are handled through the complex chain that eradicated the challenges that are followed up in file-based information. Even or the non-file-based information, these techniques are vastly used since severe information can be easily masked up without damaging any of the confidential data.
Auditing
If we move towards much more legal compliance and regulation, it has become an essential thing to audit. In such case, Big Data management can be extremely helpful since it can easily log cluster configuration and cluster access. In such cases, each and every platform is logged in so that files can be modified and changed, cluster reconfiguration, database structure modifications, attempt to login in order to use certain service and expectation of an application can be easily tackled.
In addition to this, the volume of data is increasing due to auditing and file logging. This requires a careful analysis of data or a project to eliminate any sort of redundancy. It also helps in managing the storage cost of a project.
Disaster Recovery and Backup
When a company is responsible to tackle a huge amount of data, then it is possible to face system failure at one point in time. However, with the help of Big Data, this issue is eliminated at a huge level. A system helps data majorly by making backups, mirroring files and even replicating the whole system to another. These are used widely but the main drawback is a redundancy of data.
Redundant data is of no use to the system or even enterprise that becomes a major setup for the business world. However, Big Data has come up with a solution to this problem as well. The data cannot be replicated by any means in real time. In this system, data is divided into categories – non-critical and critical, low and high time. These divisions are then stored in the system.
Big Data has become the backbone of not just IT industry but the entire business world. They are using advanced analytics tools and cloud computing with Big Data to make it even more efficient and reliable. In coming years, it won’t be surprising to see a major change in the data landscape and the approaches of data security.
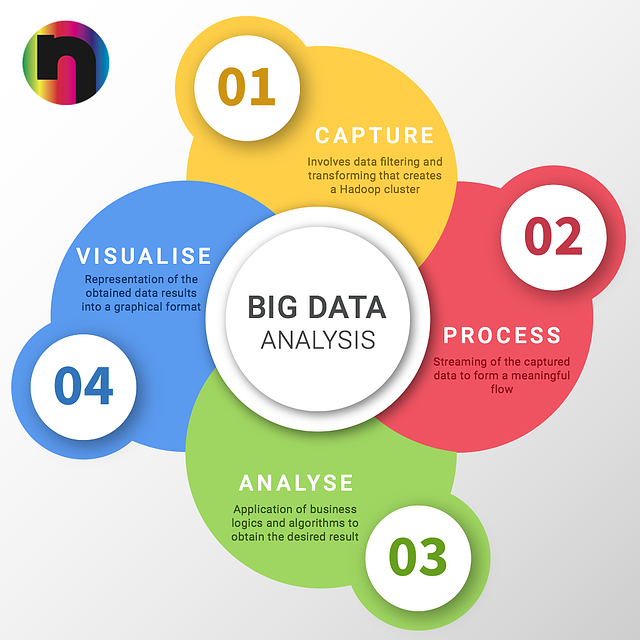
Benefits of using Big Data in Education
Data alone is nothing but the deep data analyzed can become a treasure in the form of reliable information, which can make a difference in the...