AWS vs Azure - Which one is the most suitable for your business?
Amazon Web Services and Microsoft Azure public cloud, arguably have the most elaborate and defined set of services to offer. Although there are other...

Security breaches are very common to hear when it comes to technology. Recent news updates like the one for Code Spaces security breach clearly depict how hackers gain access to console of AWS. The account was hacked because they didn’t follow a two-way authentication.

9 things to keep in mind while building a secure AWS environment:
1. A Two factor authentication is mandatory
Enable a two factor authentication and change the password of root account. The API keys associated with the root account must be revoked. Also, the data related to account must be secured at a safe location. You can provide an administrator’s account.
2. Permissions should be restricted
Only limited permissions should be granted to users such as erasing screenshots, S3 objects and volumes of data. The reason is that once data is lost here it is not possible to retrieve the data.
3. Customized privacy principles should be defined
The privacy principles should be defined even for the lowest privileges. Policies of IAM must be created. These policies monitor what users can do as well as when and where can they do it.
4. Granting account access only after proper verification
Many users would be required to be given IAM accounts. However, if they only need consolidated access, do not provide them with API keys. Here, too, a two factor authentication is a must.
5. Using secure passwords
Make the passwords more complex and fix the length to at least 12 characters.
6. Never text the credentials
Never e-mail or text your credentials. These are too easy to hack.
7. Rotate the API Keys
Keep rotating the API keys to ensure increased safety levels.
8. Audit frequently
Regular auditing helps you protect your environment. Someone should be there to manage your everyday activities going on at cloud.
9. Enable cloud trail
It is accessible in your region, enable cloud trail. This helps gathering information about who could be hacking your system and hence taking preventive measures.
For any AWS services:

Amazon Web Services and Microsoft Azure public cloud, arguably have the most elaborate and defined set of services to offer. Although there are other...
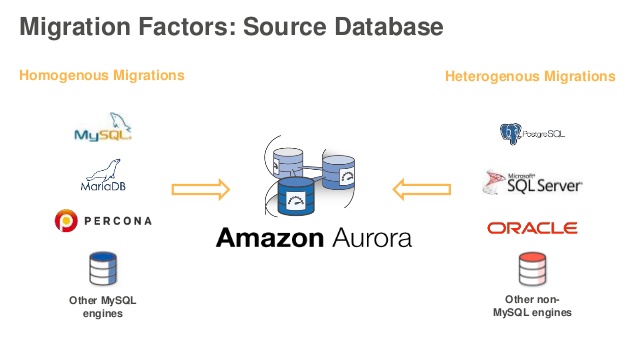
Amazon Aurora is a MySQL compatible relational database engine that combines the speed, availability, and security of high end commercial databases...

Amazon Simple Notification Service also known as Amazon SNS can now be used to receive notifications such as emails and text messages when the AWS...