5 simple ways to use Artificial Intelligence for Mobile app development
AI (Artificial Intelligence) is a computer science field that targets the improvement of smart machines which perform and react like a real person....

Ensuring top notch mobile apps security for your business application is crucial to preserve and improve your business reputation. Users are the king and it is important to ensure that their data is secured properly in your app. In the case of failure to provide good security your user’s precious data can be stolen or manipulated, your app can be injected with a virus, it can be cloned, and a doppelganger brand can emerge for your company. Ultimately you may end up wasting all your resources spent in development and end up ruining your business reputation.
Read More: How to Handle Internal & External Security Threats?
According to Arxan technology report, 90% of apps surveyed had at least 2/10 of OWASP’s top ten major security risks. Even today 50% of business don’t allocate a separate budget for mobile apps security. While this means a treat for the hackers, it can be a huge risk for businesses. To help you solve this issue we have compiled top 10 things that adversely impact the mobile apps security and how you can deal with them.

Any communication that happens between the app and the user outside the mobile phones happens through a server. Thus, this becomes a primary target that gets exploited by the hackers. The precautions you can take to ensure server side security may range from hiring a specialized security expert in-house to simply using a testing tool and taking general precautions. The major problem arises when developers do not undertake traditional server side security considerations under the account. Here are some common reasons accounting to this:
The easiest and most important step to secure your mobile apps from server side vulnerabilities is to scan them. Yes, that's it, you need to scan your apps using an automated scanner. An automated scanner brings out common issues that can be solved with little effort. It is important to do this because these scanners can also be used by hackers to find out exploits they can use to easily hack your application. If you want advanced security than you can also hire cyber experts to guide you through the process.
Read More:5 ways to secure your mobile apps
In the absence of binary protection, an adversary can reverse engineer the code of app to inject a malware or redistribute the pirated application possibly with a threat. It a critical concern in mobile apps security as it can result in confidential data theft, brand and trust damage, frauds, revenue losses etc.
To avoid this it important to use binary hardening techniques. Under binary hardening, the binary files are analyzed and modified to protect against common exploits. This allows for the fixing of vulnerabilities in the legacy code itself without the need for source code. The application should also follow secure coding techniques for jailbreak detection controls, checksum controls, certificate pinning controls and debugger detection controls.
Another common mobile apps security loophole is the lack of secure data storage. A common practice among the developers is to depend upon the client storage for the data. But client storage is not a sandbox environment where security breaches are not possible. In the event of an acquisition of the mobile by an adversary, this data can be easily accessed, manipulated and used. This can result in identity theft, reputation damage and external policy violation (PCI).
The best way to secure your data storage across platforms is to build an additional layer of encryption over the base level encryption provided by the OS. This gives a massive boost to mobile apps security and reduces your dependence on the default encryption.
Read More: How to Develop a Successful Mobile Strategy for Business?
Transport layer refers to the route through which the data is transferred from client to the server and vice versa. In the case of an insufficient transport layer a hacker can gain access to the data and modify or steal it on his will. This results in frauds, identity threats etc. A common practice is to use SSL and TLS to encrypt the communication. The problem is that not all SSL is the same. Many of these are issued by third party analytics company or are self-signed. Here are some ways to secure mobile apps by strengthening the transport layer:
Unintended data leakage refers to the storage of critical app data on insecure locations on the mobile. The data is stored in a location on the device that is easily accessible by other apps or the users. This results in the breach of user privacy leading to the unauthorized use of data. People often get confused between unintended data leakage and insecure data storage. Unauthorized data leakage is caused due to issues like OS bugs and negligence of security in the framework itself which are not in control of the developer. On the other hand, insecure data storage is caused by reasons which are in very much in knowledge and control of the developer. You can prevent unintended data leakages by monitoring common leakage points like caching, logging, application backgrounding, HTML5 data storage and browser cookie objects.
Read More: 7 Essentials tips to Develop Phenomenal Mobile Apps
Poor or missing authentication allows an adversary to anonymously operate the mobile app or backend server of the mobile app. This is fairly prevalent due to a mobile device’s input form factor. The form factor encourages short passwords that are usually based on 4-digit PINs.
Unlike in the case of traditional web apps, mobile app users are not expected to be online throughout their sessions. Mobile internet connections are not as reliable as traditional web connections. Hence, mobile apps may require offline authentication to maintain the uptime. This offline requirement can create security loopholes that developers must consider when implementing mobile authentication.
An adversary can brute force through the security logins in the offline mode and make operations on the app. In the offline mode, apps are usually unable to distinguish between users and allow users with low permissions to execute actions that are only allowed to admins or super admins. In order to prevent operation on sensitive information, it is best to limit login only in the online mode. If there is a specific business requirement to allow for offline authentication then you can encrypt the app data that can be opened only with specific operations.
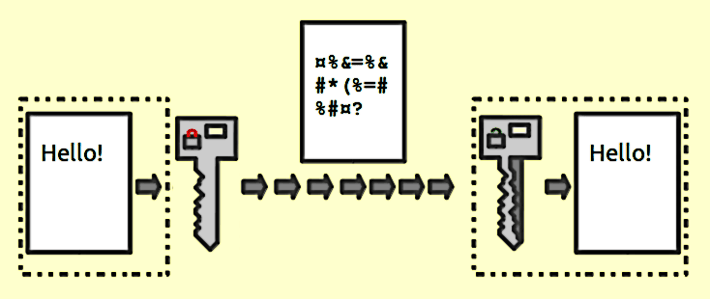
Broken cryptography is a common mobile apps security issue that arises due to bad encryption or incorrect implementation. By exploiting the vulnerabilities an adversary can decrypt the sensitive data to its original form and manipulate or steal it as per his/her convenience. Broken cryptography can result due to complete dependence on built-in encryption process, use of custom encryption protocols, use of insecure algorithms, etc. Hackers can also be benefitted from poor key management like storage of keys in easily accessible locations or avoiding hard coding of keys within the binary. The best practice is to use superior encryption protocols and proper implementation process to avoid any mistakes and perform encryption properly.
Client side injection refers to the execution of malicious code on the client side on the mobile device, via the mobile app. Typically, a threat agent inputs the malicious code into the mobile app through a number of different means. The underlying frameworks supporting the mobile app process this code like all other data on the device. During processing, this code is forces a context switch and the framework reinterprets the data as executable code. The code may either run within the scope and access permissions of the user or it can also execute with privileged permissions leading to much greater potential damage. Another form of a client-side injection includes direct injection via binary attacks. This brute-force approach has a greater potential for damage than data injections.
The best way to prevent application vulnerabilities to injection is to identify the sources of input and ensure that user/application supplied data is being subject to input validation thus, disallowing code injection. Checking the code to validate whether the application is handling data correctly is the best way to ensure the security of your mobile app. Code analysis tools can help a security analyst find the use of interpreters and trace the flow of data through the application. Once a loophole is suspected it can be confirmed by manual penetration testers who can craft exploits that confirm the vulnerability.
Developers generally use hidden fields, values or functionality to distinguish between higher and lower level users. An attacker might intercept the calls and mess with such sensitive parameters. Weak implementation of such hidden functionalities leads to improper app behavior resulting in higher level permissions being granted of to an attacker. The technique used to exploit these vulnerabilities is called hooking.
A mobile application maintains communication between clients and servers using an inter process communication (IPC) mechanism. IPC is also used to establish communication between different apps and accepting data from various sources. An adversary can intercept this communication and interfere with it to steal information or introduce malware. Here are some tips related to IPC mechanisms that you can use to improve the security of your mobile app:
Improper session handling refers to the continuance of the previous session for a long period even when the user has switched from the application. Many e-commerce companies tend to enable longer sessions to speed up the buying process and business does so to provide a better user experience by optimizing the speed. But this practice can be dangerous particularly if the phone is stolen. Any person who gains access to the device can undertake control over the application and steal or manipulate important data.
The best way to find a middle ground between speed and privacy protection is to use re-authentication for important actions like purchases or access to priority marked documents. This way you will let users have the requisite access without compromising on the mobile app security. This practice is commonly used by the Amazon mobile app. In the app, the user can browse through products at their discretion but they will need to sign in again while placing the final order.
Read More: 10 Key Metrics to Measure User Engagement on Mobile
So here we have 10 things you do that compromises mobile apps security. By following the best practices stated to solve each of these issues you can ensure a seamless and secure user experience. In return by ensuring top class security in your mobile apps, you will improve your brand identity and preserve it from potential attackers. If you are still having troubles securing your mobile apps than you are at the right place. We at NewGenApps have 11+ years of experience in developing secure mobile apps that elevate the user experience and prove successful in the market. If you have a project then do contact us today.

AI (Artificial Intelligence) is a computer science field that targets the improvement of smart machines which perform and react like a real person....

Mobile app development is an ever-growing industry with new applications and uses cases coming every day. But it is not only the use cases that are...

So you have a great idea for a mobile app. You might also believe it to be a breakthrough concept. It is a common misconception among would-be...